Chinese researchers have discovered cyber widely spread the GhostDNS malicious campaign that has captured more than 100,000 home routers and changed their DNS settings for users to crack malicious web pages, especially if they visit banking sites, and steal their credentials.
GhostDNS Dubbed, the campaign has a lot to do with the notorious malicious software DNSChanger, which works by changing the DNS server settings on the infected device, allowing hackers to route Internet traffic with a malicious server and steal confidential data.
According to a new report from the company Netbab Qihoo 360 on cybersecurity like normal DNSChanger campaign, GhostDNS scans the IP addresses for routers that use little or no password, refer to the router settings, then change the DNS-address from the default router to a controlled attack.
GhostDNS system: a list of modules and submodules
The GhostDNS system essentially consists of four modules:
1) DNSChanger module: this is the main module of GhostDNS, intended for the use of target routers based on the information collected.
module DNSChanger consists of three sub-modules, which the researchers have named, Shell DNSChanger, Js DNSChanger and PyPhp DNSChanger.
Also Read: How To Check If Your Twitter Account Has Been Hacked
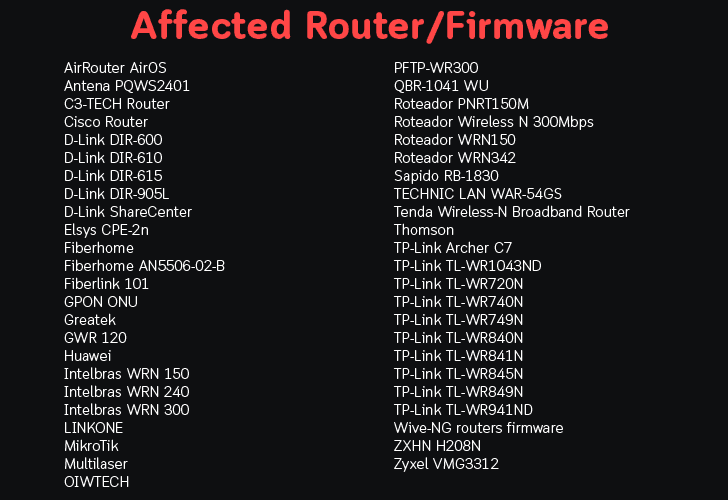
a.) Shell DNSChanger. This sub-module is written in the Shell programming language, includes 25 shell scripts that can drag passwords on routers or firmware packages from 21 different manufacturers.
b.) Js DNSChanger. This text is primarily intended for JavaScript, which includes 10 attack scenarios designed to infect 6 routers or software packages.
“Its functional structure is essentially divided into scanners, payload generators, and attack programs. The DNSChanger Js program is usually introduced in phishing sites, so it works with the phishing web system,” say the researchers.
c) DNSChanger PyPhp. This sub-module is written in Python and PHP, contains 69 different attack scenarios against 47 different router/firmware and has been found deployed on more than 100 servers, most of which are located in the Google Cloud and includes features such as the Web API, scanner and attack module.
This sub-module is the main module of DNSChanger, which allows attackers to scan the Internet for vulnerable routers.
2) Web Admin: Although the researchers do not have much information about this module, it seems that it is the attacker’s administration panel provided with the login page.
3) Unreliable DNS module. This module is responsible for resolving domain names targeted by an attacker-controlled web server, primarily related to banking and cloud hosting, and security-owned domain-based company Avira.
“We do not have access to Rouge DNS server, so we can not tell exactly how many DNS-names had been captured, but, referring to Alexa Top1M and our domains Top1M DNSMon vs. Rogue DNS Server (139.60.162.188) , we were able to find a total of 52 domains were captured, “say NetLab researchers.
4) Phishing web module. When the target domain is successfully resolved through the unreliable DNS module, the phishing web module targets the server with the wrong version appropriate for that particular website.
The malicious GhostDNS program targets Brazilian users first
According to the researchers, from September 21st to 27th, the GhostDNS campaign has compromised more than 100,000 routers, 87.8% (87,800 people) are located in Brazil alone, which means that Brazil is the main target of attackers GhostDNS.
Also Read: Researchers Developed DeepLocker Artificial Intelligence- Powered Stealthy Malware
“Currently, the campaign is mainly focused on Brazil, we have calculated the IP addresses of 100 000+ infected IP addresses (87.8% in Brazil), as well as more than 70 routers/firmware and more than 50 domain names, banks in Brazil, even Netflix, Citibank.br were hijacked to steal the appropriate credentials to access the site, “said the researchers.
Because the GhostDNS campaign is highly scalable, it uses a different attack vector and takes an automated attack process, which creates a real threat to users. As a result, users are encouraged to protect themselves.
How to protect your home router from hackers
In order not to fall victim to such attacks, it is advisable to make sure that your router uses the latest firmware and sets a strong password for the router’s web portal.
You may also consider disabling remote administration, changing the default local IP address, and encrypting a trusted DNS server on your router or operating system.
NetLab researchers have also recommended that router providers increase the complexity of the default password for the router and improve the mechanism for updating system security for their products.



