Man In The Middle Attack Over SSL
A group of security researchers found a critical man in the middle attack implementation gap in the main mobile banking applications that left the banking powers of millions of users vulnerable to hackers.
The vulnerability was discovered by security groups investigators and privacy at the University of Birmingham, which is checked hundreds of different banking applications – such as iOS and Android – and found that some of them have been affected by a problem common as a result of which its users are vulnerable to man in the middle attack in the center.
The affected banking applications include HSBC, NatWest, Co-op, Santander and Allied Irish Bank, which are now being updated after researchers informed them.
Also Read: HP Is Secretly Installing Telemetry Bloatware On Your PC- This Is How You Can Remove It
According to a study published by researchers [PDF], vulnerable applications could allow a malicious user connected to the same network as the victim, to intercept SSL connection and obtain user credentials, such as usernames and passwords / PIN code, even if the applications use the bind SSL function.
The SSL link is a security feature that prevents human attacks in the medium (Man In The Middle Attack), providing an additional level of trust between the hosts and devices listed.
When this is done, protecting SSL helps to neutralize network attacks in which attackers can try to use valid certificates issued by dishonest certification authorities.
“If a CA has acted in bad faith or has been compromised, has happened before, can be created by valid certificates for any domain, allows an attacker” Man in the middle attack “of all applications to rely on this certificate CA “, -, wrote the researchers in their article.
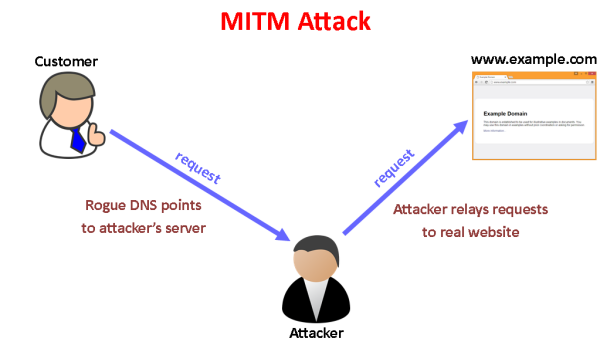
However, there are two key parts to verifying the SSL connection: the first (authentication) is to verify if the certificate is a reliable source, and the second (authorization) is to make sure that the server you are connecting to represents the correct certificate.
Also Read: MailSploit Email Spoofing Flaw Already Affected 30 Popular Email Clients
The researchers found that due to the lack of verification of the hostname, several banking applications did not verify if they are connected to a reliable source.
The hostname verification ensures that the hostname in the URL to which the banking application connects matches the hostname in the digital certificate sent by the server as part of the SSL connection.
“Vulnerabilities associated with an incorrect configuration of the TLS, apparently common, but none of the existing frameworks do not discover that the client joins the root or the intermediate certificate, but does not check the hostname in the list”, – says The document.
In addition to this problem, researchers also describe in detail the “identity theft attack in the annex” that affects Santander and Allied Irish Banks, which could allow an attacker to capture the victim’s screen at the time of the attack. request and use it to phishing credentials for the victim’s user,
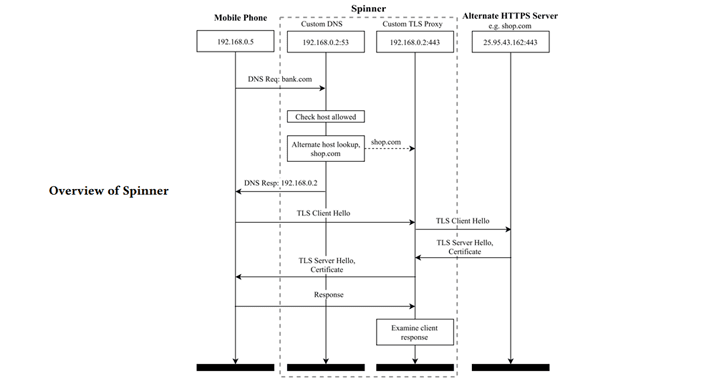
To quickly test this vulnerability in hundreds of banking applications and not require the purchase of certificates, the researchers created a new automated tool called Spinner.
Also Read: This Facebook Bug Allowed Everyone To Delete Anyone’s Photo
Spinner uses the Census IoT search engine to find certificate chains for alternative hosts that differ only in the leaf certificate.
“Given the certificate for the destination domain, the tool queries the certificate chains for alternative hosts that differ only in the leaf certificate.” The tool then redirects the traffic of the application under test to a website that has a certificate signed with the same CA certificate, but, of course, another common name, the researchers explain.
“If the connection fails during the installation phase, we know that the application detected an incorrect hostname.
Taking into account that if the connection is established and the data of the encrypted application is transmitted by the client before the connection fails, we know that the application has accepted the hostname and is vulnerable “.
Trio Chris McMahon Stone, Tom Chothia and Flavio D. Garcia worked with the National Cybersecurity Center (NSCS), to notify all affected banks, that problems are resolved before then publicly revealed their research this week.



