My roommate, who has been in the IT niche for around 6 years, has recently started doing bug bounty (s). It was extremely satisfying to hear his stories of hacking some companies and getting rewarded for doing so. So I decided to give it a shot myself.
Since I’m still a rookie in the bug bounty world, I’ve naturally been looking for Internet guides. I was surprised not to find many bug bounty guides, so I decided to take note of my friend’s process and write my own. I hope you find it useful and can take away a few tools which can improve your workflow.
Stuff to know before getting started:
- What is the scope?
- What you should and shouldn’t test?
- What tools, services, and methods you are allowed to use during the test?
- What type of reports and vulnerabilities are accepted?
- Which vulnerabilities have already been found (If public disclosure on HackerOne for instance)?
- What is the money reward?
This will help you understand the purpose of the bug bounty. It will also help you keep focused and not get distracted by unnecessary tasks in the process. Keep note that you have to use the allowed (and legal) scanners and tools so that you don’t run into problems. You need to be confident in what you’re doing, so it’s best to go over the task with your issuer in detail. Now let’s dive in and find out the basics of performing a penetration test.
Subdomain Enumeration
Let’s start with the subdomain enumeration. This process entails finding valid (resolvable) subdomains for one or more domains.
In this step, I use a service called Spyse. It’s a cyberspace search engine that crawls the entire internet with a certain frequency using OSINT. It’s super handy because all data is stored and available for access via their database, so there’s no need to wait for a scan every time you need something. I also use this service for receiving data about DNS, open ports, banners, IP addresses, and lots of other useful stuff.
The other tool is Sublist3r. This is a python tool made to enumerate subdomains of websites using OSINT. If you are well familiar with the web, this is an excellent tool as Spyse only has a python wrapper for now. It’s in beta, for now; hopefully, the CLI will be done in the coming months.
The Global-View of a Target Infrastructure
A few months ago, during my real rookie stages, I would just jump straight into finding vulnerabilities without doing recon. Then I realized that I’m doing everything backward – how can I find vulnerabilities without an idea of the network’s cartography?
Since then, I’ve used SiteMap for a global view of the target website. When I list endpoints, pages, folders, files, and other useful things, I get the following info:
- Public pages we can access without a user account
- Private pages, only accessible with a user account
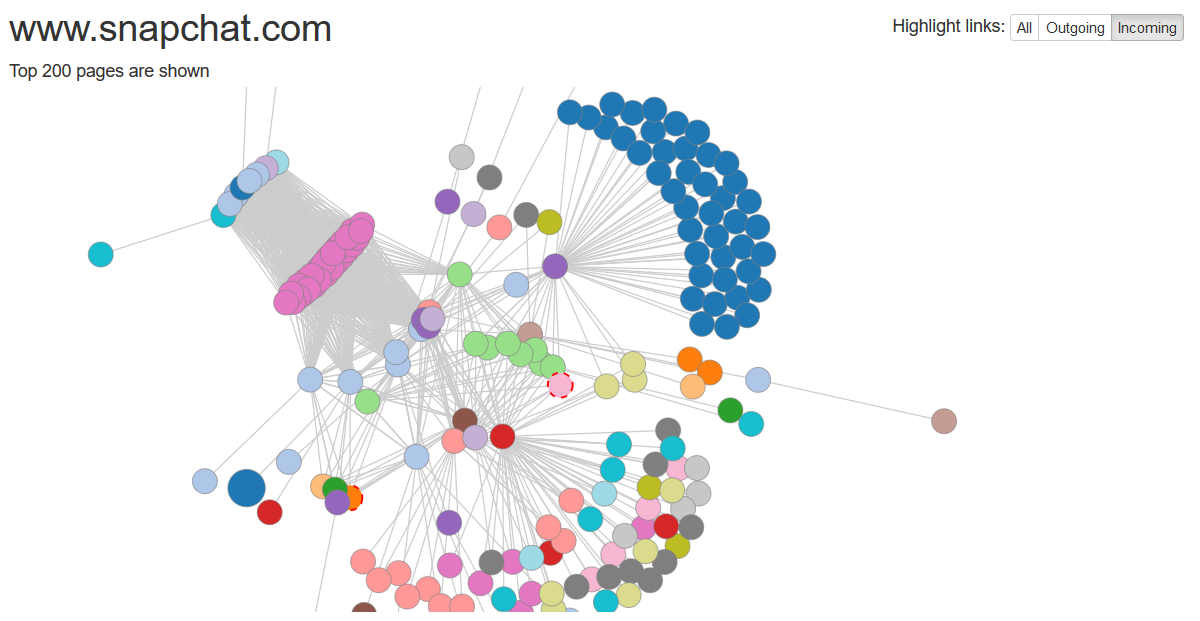
I use the Visual Site Mapper tool (www.visualsitemapper.com) to create a “global picture” of my target. This tool creates a graphical sitemap, which is very useful in listing public URLs and understanding how a website works, and what it interacts with.
After gaining a list of interesting URLs, I check them with GET parameters. While doing several bug bounties, I’ve discovered that these URLs were always more interesting. This is the part where I do manual tests because scripts can’t replace manual testing for everything. I do this to find SQL / XSS injections.
Before you commence searching for vulnerabilities, it’s also important to know what technology your target is using. Here’s what you should find out:
- Do they use a WAF like CloudFront or CloudFlare?
- Do they use a CMS like WordPress, Magneto, or Drupal?
- Do they use a framework like AngularJS?
- What’s the version of Apache?
- Do they use template engines like Jinja2 or Smarty?
After learning what technology they use (and what versions, so you can get the same ones), your vulnerability search process will blast off.
For example: say your target has a profile page where you can control the input (like a name or a nickname), which is reflected on a public page. Knowing the framework version, you may try XSS PayLoads or other payloads.
Also Read: How To Find Vulnerable Webcams Around The World
If your target chooses a template engine like Smarty, check their version of the engine and use template injection. I use the plugin Wappalyzer.

Wappalyzer works as a straightforward plugin that displays lots of interesting information about your target. It shows the technology they used, and what version of it.
Recon With Google Dorks
Let’s not all forget about Google Dorks. It can be used for recon as it indexes various URLs and files, and extracting them could lead to fruitful results.
Here’s how you can try to use Google Dorks:
site:target.com filetype:pdf,xml,pps
site:target.com intitle:”test” -support
site:target.com ext:php | ext:html
site:target.com inurl:auth
site:target.com inurl:dev
Deep investigation
This is where Spyse comes in handy again. It’s just like a simple search engine, except it looks for servers. You can also use some “dorks” to improve your search. Here are the things you can search for with Spyse:
- IPv4 Hosts
- Autonomous Systems
- DNS records
- SSL/TLS certificates
- Domains and Subdomains (they got the biggest subdomain database available)
For now, that’s all they have, but it’s a great starting point for this service. They aim to create a full cyberspace search engine. Soon they’ll have the option of seeing versions of technologies, devices, previously found vulnerabilities, and more. I can’t wait, as this sounds like a Swiss army knife for white hats like me.
Here are some other useful tools you can use:
Dirsearch: a simple web path scanner. Search for directories with default wordlist and all (*) extensions.
https://github.com/maurosoria/dirsearch
Burp Suite This is a Java-based Web Penetration Testing framework that quickly became an industry-standard suite of tools used by information security professionals. Burp Suite helps users find vulnerabilities and verify attack vectors that are affecting web applications.
WebScreenshot – for visual recon.
IP range Crawl
This can also be done using Spyse.
Domain Profiler – usually not so useful, but interesting
https://github.com/jpf/domain-profiler
Domain Analyzer – Analyze the security of any domain by using a bunch of different info.