In the new ransom attack (Petya Ransomware) is currently attacking a large number of countries all over the world, including Ukraine, the UK, India, the Netherlands, Spain, Denmark and much more.
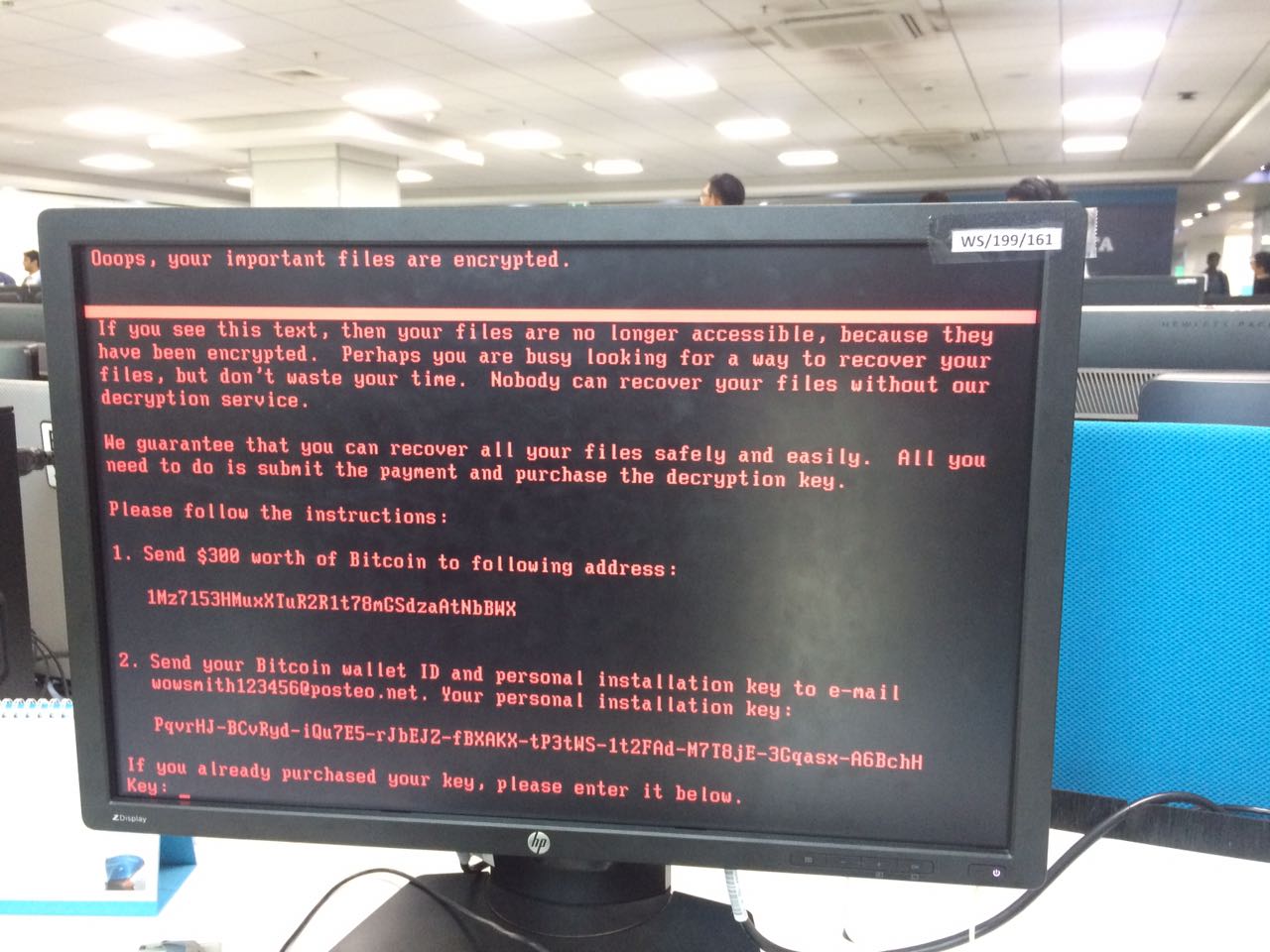
Used to grab a new ransom Contact details [email protected] requires a $ 300 payment in your home.
Malware is spreading rapidly using the same vulnerability as SMBv1 and Windows WannaCry ransom is used to attack 300000 devices worldwide.
In fact, Petya Ransomware is different, malware does not encrypt files or block in one system goal after another.
Petya Ransomware Reboot Hardware Targets and Format / Table The main file blocks of the hard drive (MFT), a database that is storing information about each file and directory on an NTFS volume.
Malicious software becomes malfunctioning Master Boot Record (MBR), which limits access to the entire system by capturing information about file names, sizes, and location on the physical hard disk.
Then replace the master boot record (MBR) of the device by malicious code with malicious code that represents a ransom note and leaves the devices unable to boot.
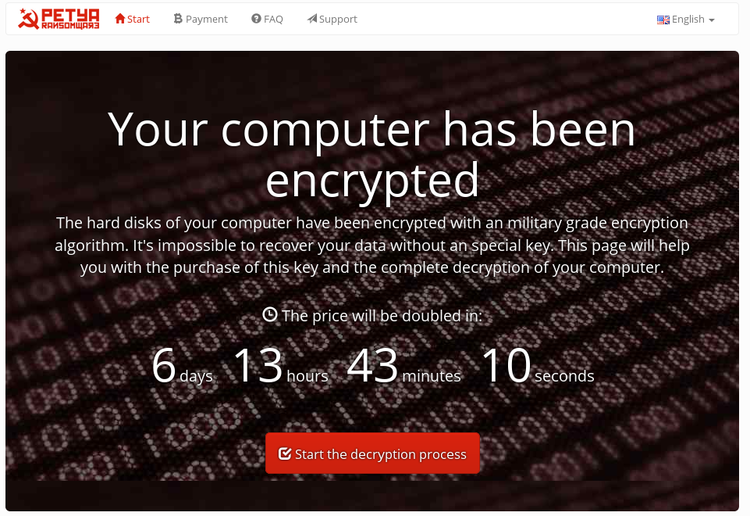
Ransom says:
“If you see this text, the files are no longer available because they are encrypted, and maybe you’re busy looking for a way to recover your files, but do not waste your time … Nobody can recover your files without our decryption service.”
How Petya Ransomware Is Spreading Widely?
Symantec, the cybersecurity security company, also confirmed that Petya Ransomware exploits SMBv1 EternaalBlue exploit, as do deniers, make use of Windows machines are not installed.
“Petya Ransomware’s successful deployment, as it combines both in client-side attack (palm-2017-0199) and threat-based network (MS17-010),” security researcher using the Hakervantastic Twitter handle Tweeted.
EternalBlue is exploiting Windows SMP filtered by the group of notorious piracy shadow brokers in April, which claimed that it had stolen from the CIA and CIA along with other Windows exploits the data dump.
Microsoft has since corrected the weakness for all versions of Windows operating systems, but many users remain vulnerable, and a number of malware variants exploit the bug to provide Ransoumouar and mine Krebtukerance.
Just three days ago, we were informed about the last wanna cry attack that hit Honda Motor Co. and about 55-speed cameras and light traffic cameras in Japan and Australia, respectively.
Well, it is quite surprising that even after knowing the cause and Wanna cry for a sufficient period of time, large corporations and corporations still do not take appropriate security measures to defend themselves against this threat implemented.
Petya Ransomware Attacked Banks, Telecom, Businesses & Power Companies
Petya Ransomware has already reached – The state-owned Rosneft giant, and state power companies of Ukraine, “Kyivenergo” and “Ookrenerg”, in the last hours.
The news agency said Kyivenergo “We were attacked, two hours before we have to shut down all the computers we have, and we are waiting for authorization from the Ukrainian security service repeat.”
There are reports from several banks, including the National Bank of Ukraine (Nebo) and Ooscadbank, as well as other companies confirm that they had been beaten by Petya Ransomware attacks.
Maersk also confirmed, an international logistics company, on Twitter that the latest Petya Ransomware attacks closed information technology in multiple locations and business unit systems.
“We can confirm that Maersk’s information technology systems are declining in various locations and work units, and we are currently working to confirm the situation, as the safety of our employees and our operations and our customers are our top priority, and We will update when we have more information, “the company said.
Petya Ransomware also affects several workstations in the mining sector of the Ukrainian company in the secretion.
Includes the most serious damage Ukrainian companies also reported risk systems in the local metro in Ukraine and the Borispol airport in Kiev.
Three Ukrainian telecommunication operators, Kyivstar, LifeCell, Ukrtelecom, are also affected by the latest Petya attack.
How to protect yourself from Petya Ransomware attacks
What needs to be done immediately? Go and apply patches against the Aturnalbulo curse (MS17-010) and disable the SMBv1 file sharing protocol is secured, at the age of 30 on Windows systems and servers of its own.
Since Petya Ransomware also makes use of tools and Mick and Bsaxhex to infect Windows computers with all patches, it is also recommended to disable and (Mick Windows Device Manager command line).
Prevent infection and Petya’s switch agent
Researcher Petya encryption systems Ransoumouar finds after restarting the computer. Even if your system is infected with Petya Ransomware and tries to reboot, you just will not force it again.
“If the device reboots and this message appears, turn off the power immediately! This is an encryption process you do not work, the files are fine.” Hakervantastic makes a sound.
Little Sakurete was discovered, the cyber security company based in the UK, switch agent Petya Ransomware for. According to the tweet, the company advises users to create a file, for example, “C: \ Windows \ Perfc” to prevent Ransomware infection.
Protection against any Ransomware infection, you should always be suspicious of unwanted files and documents sent by email and, you should never click on links inside unless you have verified the source.
You have always tightened on your valuable data hold, keep a good backup routine in place that makes the copy on an external storage device is always connected to your computer.
Also, be sure to run the anti-virus security suite is well and effectively in the system, keep up to date. Most importantly, always surf the Internet safely.



